Movicon.NExT Help on Line - Rel. 4.2.358
To get a Movicon.NExT project 21CFR Part 11 ready, you will need to configure it appropriately so that it is compatible with the FDA validation criteria. The necessary measures to take in doing this are indicated below:
Project Security
The project must be configured in its General Properties by selecting Project Password and setting a protection password. In this case, access to the project in design mode will be protected and all the project’s XML will be encrypted and inaccessible due to a proprietary algorithm.

Confirming this operation will save all the Movicon.NExT project files with encryption and protection when the project is next opened. It is important to remember that projects protected with passwords can be executed in runtime but cannot be modified or accessed in design mode without using a password to gain access.
System Startup
When turning on the PC, the Windows operating system will startup together with the Movicon.NExT platform by automatically launching the project. For security purposes, these operations should be configured appropriately to ensure that the project is started up safely in protection mode.
At Windows startup, all the Movicon.NExT project Server components should be run automatically using the Windows Services’ functions. The Movicon.NExT project should therefore provide Services management using a control panel that can be accessed from the Movicon.NExT Editor. This Editor is used to install the Server parts (such as the I/O Server, Schedulers, Recipes and other) as Windows Services. In this way, they will all be run automatically when starting up the operating system independently from the Windows User Log On.
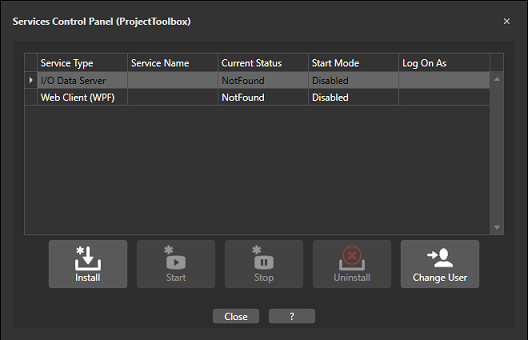
The Services Control Panel accessed by means of the Movicon.NExT Editor
The Windows’ user interface can only be accessed when Windows user has been authenticated. As a consequence, the Movicon.NExT user interface, known as the Client, will only be available after the Windows’ User has Logged on successfully. There are several options to use for doing this:
Windows startup in normal mode by means of Windows user log on. The desktop interface will not be available until a Windows user has logged on. After a user has logged on with Windows, the startup applications can be run and then a command line can be executed to startup the Movicon.NExT Client. The Movicon.NExT Client project will then manage security and the project user management as well as consenting access to the Windows Desktop.
The Windows startup can be put into operation by setting the operating system to automatically log on a Windows user for default by means of using the operating system’s startup command string. In this case, Windows will startup with an enabled ‘standard’ user, and as a consequence so will the Movicon.NExT Client startup automatically. The Movicon.NExT Client project will then manage the security and project users management as well as consent access to the Windows Desktop.
The Windows and Movicon.NExT user management can be shared. Movicon.NExT permits shared Windows User Domain, and as a consequence the Windows user Log On will permit Windows authentication and the startup of the Movicon.NExT Client project. In this case, the Movicon.NExT project users will be shared with those of the Windows operating system domain.
Windows can also startup without the Desktop (including the resource explorer and management), and therefore by starting up the Movicon.NExT Client only by impeding any access to the Windows Desktop.
In any case, access to the Windows desktop or its exclusion, and the configuration of Windows user privileges does not depend on Movicon.NExT, and must be managed by the system administrator.
Access to the Windows user interface (Desktop)
While in operation, therefore after the startup of Windows and the Movicon.NExT project application, it is important to manage the operating system’s functions that consent access to the desktop from the application in the right way.
According to which mode the operating system was started up in, the user has the option to manage controlled Desktop access by means of the access level settings associable to the project user passwords.
When the Movicon.NExT user interface (Client) is running, unauthorized access to the Windows user interface (Desktop) can be blocked by eliciting Movicon.NExT user authentication request for users with Desktop access privileges. User role requests can be assigned to users with Desktop access by means of using the Movicon.NExT General User Management properties.
The operation system can also be configured to exclude the Windows Desktop in order to use the Movicon.NExT user interface functions only. This configuration must be done by a system administrator.
All the application commands that can be executed by operators to interact on the process must be protected by passwords.
The password management must be enabled in the project’s User Password resource’s General Properties.
Enable Password Management: the passwords will be activated according to the levels and access modalities to the preset commands.
Auto Logoff: determines the time (sec.) for automatically deactivating the active user after a period of inactivity.
Minimum Password length: sets the minimum password length allowed (4 characters for default).
Electronic Signature Definition: the unique user Description of the user whose name is to be used as an Electronic Signature will be managed.
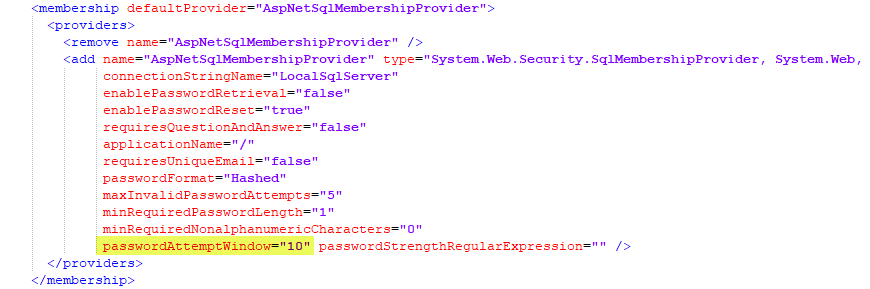
Movicon.NExT will automatically control correct authentications, the uniqueness of the Electronic Signatures and any attempts to force User Log On. Any further Log on attempts made after the fifth one fails, will be recorded in the Event Log and the response time will deliberately take longer to discourage further attempts.
|
The number of login attempts can be set in the Membership section found in the “MoviconNExT.exe.config” system file as shown below. |
Each user or user group, who have access to commands or process interaction, must be inserted and configured in the project appropriately.
Users are inserted in the project’s User Password Resource where they can be configured in their properties. These properties include those which conform to the FDA regulatory requirements:
Name (ID) and Password. These are assigned to the user and are used for identification by the system.
This is a unique text which corresponds to the user’s electronic signature and is recorded as absolute user identification (the Electronic Signature management must be enabled in the User Password Resource)
Auto Log Off: user deactivation time to be used after a period of inactivity.
Expiring Password: The act stipulates that the user password expires after a certain preset time so that the user is obliged to change it periodically to increase system security.
Change Password after first login: the normative requires that user be made to change their password once Logging in to prevent the administrator who inserted the original password from knowing it and thus contributing more to identification certainty.
Comments on Alarm Acknowledgements (Audit Trail)
In many cases, before the operator is allowed to acknowledge an alarm, they may be required to make a comment, which will then be recorded in the historical together with the alarm ACK event.
Movicon.NExT provides a function where a severity level for each individual alarm is specified and in addition to which the Movicon.NExT Alarm window will ask the user to enter a comment on the acknowledgement operation.
Therefore, it will be necessary to define the alarm’s severity level and threshold level that once reached will ask the operator user to enter a comment on the operation performed.
A severity level must be defined in the properties of each alarm.
The priority threshold level must be defined the Alarm Window properties that once exceeded will force the operator to enter a comment on the acknowledgement operation for Auditing purposes.
Comments will be recorded in the Events log with the acknowledgement operation.
An User Access Level can also be set for executing operations in alarms.
Data Storage Security and Validity
Protecting the storage of recorded data against manipulation of Electronic Records is absolutely essential to obtain validation and conformity with the CFR21 regulations and their application.
Data recorded by Movicon.NExT (Audit, Historian, Data Loggers) are physically created with database file archives. In order to ensure an effective data validation system, Movicon requires the use of the Microsoft SQL Server as a database for recording data. Projects can use other types of databases for storing data but if you need to have a FDA CFR21 Part 11 compliant, the Movicon.NExT stored data integrity validation system is based on secure control mechanisms that the require the exclusive use of the Microsoft SQL Server. It is therefore absolutely crucial that you comply with the system configurations and project design constraints described in the product documentation. Succinctly, Movicon.NExT validation system provides a mechanism to record data on databases using a data uniqueness criterion based on the encrypted Movicon.NExT User system and specific controls from the SQL Server system’s Transaction Log. Therefore, Movicon will record data using a unique and encrypted Windows System User in association with the database’s Transaction Log to control and detect any undesired manipulations.
This pre-validated database containing information on the process and each Logged transaction will safeguard stored files submitted for validation from any undesired manipulation or modification.
This ensures that the file is analyzed in its original form and validated through a Viewer designed to detect and alert any manipulation to data upon which validation of such file will be withheld.
In addition to the above mentioned content, it is the responsibility of the user to implement the necessary data security and integrity criteria by configuring the database with the most adequate data access protection and retention systems that can ensure data availability for an appropriate period of time with reliable redundancy and backup systems as stipulated by the regulations.
Electronic Records
By Electronic Records we mean all production process information (data, values, events) electronically recorded in archives that ensure data integrity and protection against undesired manipulation.
All the information that Movicon.NExT records in database archives can be defined as ‘Electronic Records’.
In order for the Movicon.NExT Electronic Records to be compliant with the regulations, you will need to follow the indications and guide lines contained in this document and in the user manual to ensure data integrity and security and prevent unauthorized data access or manipulation.
Data recorded on the SQL Server database within the constraints of project design and application and with the relative intrinsic security criteria, are submittable for validation and authentication in order to ensure the originality of data and therefore to impede any type of unwanted manipulation.
Movicon.NExT manages a recorded data validation system that can be activated by means of using the historical data management property settings configuration. This is done by checking the Enable Event Data Protection property in the Database Settings properties of the recording engines managed by the Movicon.NExT Server.
When enabling this function, Movicon.NExT will use an encrypted System User ID and Transaction Log combination to ensure the integrity of each individual data recorded (records) on DB.
Aided by this control, Movicon.NExT can ensure users that the data recorded is genuine and impede any possible manipulation to alter or cancel the data.
|
Each historical data storage system can therefore be subjected to validation controls in Movicon.NExT, to confirm data authenticity or detect any data tampering. |
Users operating in systems subjected to CFR21 validation, will be able to ensure data authenticity by implementing it where needed using data protection management or data visualization or print validation checks.
When enabling the data protection management, it will be impossible for anyone to tamper with historical data recorded by Movicon.NExT as validation checks are run to validate data authenticity or highlight any alterations due to unauthorized tampering.
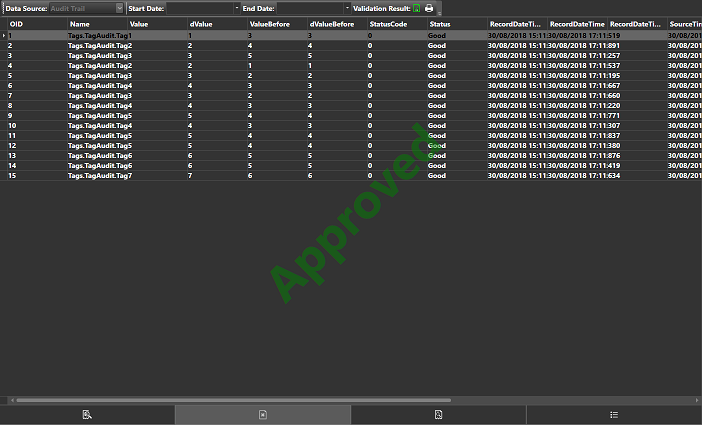
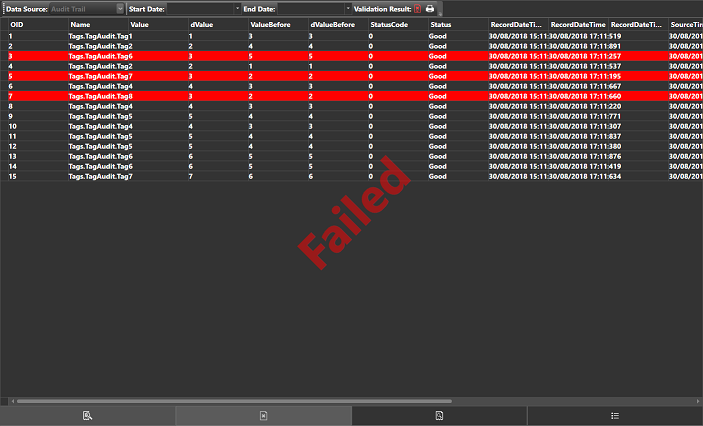
This screen shot shows Historical database subjected to validation with positive results. Instead, the screen shot below shows the same check on a tampered and unauthentic historical database.
Data Retention
Historical data must be made available in storage for an adequate period of time according to the process managed. The period of time can be defined as needed in the Movicon.NExT recording engine and independently from the time of databased being used. Object properties allow the number of days (e.g. 730 days can be set to cover 2 years) for which the application will ensure data availability. Once this period has been reached, the oldest data will be overwritten by the most recent to ensure that data is retained for availability for the period of time desired.
Data backup can be managed as desired in the project using the script functions to manage the data sources and destination backup files, or third party backup tools can also be used instead.
Redundancy
Movicon.NExT totally supports the multi-server redundancy function, not just for archive synchronization but also for any operating functionality automatically and transparently. The Redundancy function should be applied and managed in a way that complies to the regulations and in function with the process type.
The Redundancy function allows Movicon.NExT to synchronize the historical archives in a number of servers to ensure both maximum data and operation reliability.
External Security for DB archives
By means of using the Movicon.NExT Server functions, process data are recorded on the configured database. These data, therefore, physically reside in files and tables that can be recorded locally on hard disk or in mass archives that physically reside in several servers, or in the Cloud. With the aid of safe relational databases, such as the SQL Server, Movicon.NExT uses protected connections (accounts) for accessing files. It is the responsibility of the user to configure the system so that no one can access files, by removing access rights to files both in the actual database and in the access privileges to folders by the operating system (Movicon.NExT run as service).
It is necessary to ensure data security by using this procedure:
Movicon.NExT supports any type of relational database for storing data. However, to ensure that the right validation mechanisms are used, you must use the Ms SQL Server.
To avoid unauthorized access to files, User Account protection will need to be setup by using the access criteria explicitly for system administrators or program designers only (eg. With the same project protection password). This will impede access to data tables where authorization has not been provided.
Use the operating system’s access lock (Locked by Movicon.NExT) or access rights to operating system by using Movicon.NExT as Service. By doing this, file access through the operating system will be physically denied.
Do not share folders or disks when the station is operating in net, except for system administrator access.
Remove all rights to modify database records (Updates). Movicon.NExT lets new records to be inserted whose data cannot be accessed for altering no matter what the reason is.