![]()
The OPC UA Server might automatically insert the "Platform.NExT.v2 IOServer [thumbprint].der" certificate in the list of Rejected certificates. In this case, simply move it to the list of Trusted certificates.
Movicon.NExT Help on Line - Rel. 4.2.358
Movicon.NExT uses public key certificates (X.509) as a reliable and safe tool through which public keys are exchanged with guaranteed authenticity and integrity wthin an OPC UA communication context.
These certificates are generated automatically during the setup phase and include the following:
Certificate File |
Application/Service |
"Platform.NExT.v2 Web Server [thumbprint].der" |
WebHMI |
"Platform.NExT.v2 Scheduler [thumbprint].der" |
Scheduler Server |
"Platform.NExT.v2 AlarmDispatcher [thumbprint].der" |
Alarm Dispatcher |
"Platform.NExT.v2 lOServer [thumbprint].der" |
I/O Data Server |
"Platform.NExT.v2 MoviconNExT [thumbprint].der" |
OPC UA Browser /Client Movicon.NExT |
and are found at this location: "%ProgramData%\OPC Foundation\CertificateStores\MachineDefault\certs\"
Movicon.NExT, in addtion to the certificate repository of its applications/services, provides another two folder files:
Trusted Certificates: "%ProgramData%\OPC Foundation\CertificateStores\UA Applications\certs"
Rejected Certificates: "%ProgramData%\OPC Foundation\RejectedCertificates\certs"
How to automatically accept untrusted certificates
Untrusted certificates can be accepted automatically, and therefore inserted in the Trusted Certificates folder, by using configuration options provided.
To make that, for example, the I/O Data Server automatically accept third party OPC UA Client certificates, simple set the <AutoAcceptUntrustedCertificates>true</AutoAcceptUntrustedCertificates>
option in the "UFUAServer.UAServer.Config" files found in the Movicon.NExT installation folder.
To make the Client or OPC UA Browser automatically accept third party OPC UA Server certificates, simply set the <AutoAcceptUntrustedCertificates>true</AutoAcceptUntrustedCertificates>
option in the "OPCUAClient.Config" file found in the Movicon.NExT installation folder.
Movicon.NExT Client <--> Movicon.NExT I/O Data Server (Users Management)
When using the Movicon.NExT Users Management, data exchanged between Client and Server
takes place with the "Sign" security policy by means of using certificates.
In this condition, if the the project has been configured with distributed Client and Server architecture, the exchange of security certificates between Server and Client will be needed:
This is established by copying the "Platform.NExT.v2 lOServer [thumbprint].der" file of the PC where the I/O Data Server is running in the Trusted Certificates folder of the PC where the Movicon.NExT Client is running.
Movicon.NExT I/O Data Server <--> third party OPC UA Client
This example shows how to exchange certificates manually to put third party OPC UA Client in communication with Movicon.NExT I/O Data Server.
In this case simply:
copy the "Platform.NExT.v2 lOServer [thumbprint].der" file in the third party OPC UA Trusted Certificates folder.
copy the third party OPC UA Client's certificate file in Movicon.NExT's Trusted Certificates folder.
Movicon.NExT OPC UA Client Driver <--> Third Party OPC UA Server
This example shows you how to manually exchange certificates to put the Movicon.NExT I/O Data Server in communication with a third party OPC UA Server by means of using OPC UA Client communication driver, simply:
copy
the "Platform.NExT.v2 lOServer [thumbprint].der" file in
the third party OPC UA Server's Trusted certificates folder.
When importing Tags in the project using OPC UA, it will be necessary
to also copy the "Platform.NExT.v2 MoviconNExT [thumbprint].der"
certificate in the third party OPC UA Server as indicated in the next
paragraph.
copy the third party OPC UA Server certificates file in Movicon.NExT's Trusted Certificates folder.
|
The OPC UA Server might automatically insert the "Platform.NExT.v2 IOServer [thumbprint].der" certificate in the list of Rejected certificates. In this case, simply move it to the list of Trusted certificates. |
Movicon.NExT Client/OPC UA Browser <--> Third Party OPC UA Server
This example will show you how to exchange certificates manually for putting the Movicon.NExT Client or OPC UA Browser in communication with a third party OPC UA Server, simply
copy the "Platform.NExT.v2 MoviconNExT [thumbprint].der" file third party OPC UA Server's Trusted certificates folder.
copy the third party OPC UA Server certificates file in Movicon.NExT's Trusted Certificates folder.
|
The OPC UA Server might automatically insert the "Platform.NExT.v2 IOServer [thumbprint].der" certificate in the list of Rejected certificates. In this case, simply move it to the list of Trusted certificates. |
I/O Data Server Certificate Folder
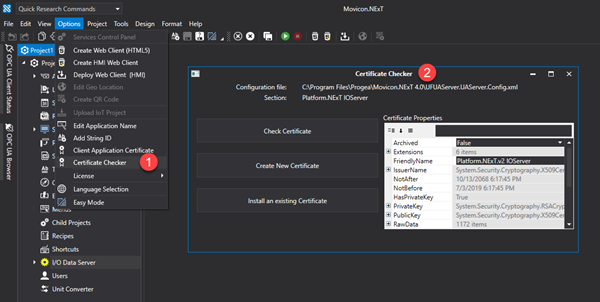
The certificate of the Movicon.NExT Server side called "Platform.NExT.v2 IOServer" may be checked, renewed or replaced using the configuration tool which is accessible (1) by expanding the I/O Data Server resource, (2) and selecting the Settings item and then (3) Selecting the Certificate Checker.
Client/OPC UA Browser Certificates Management
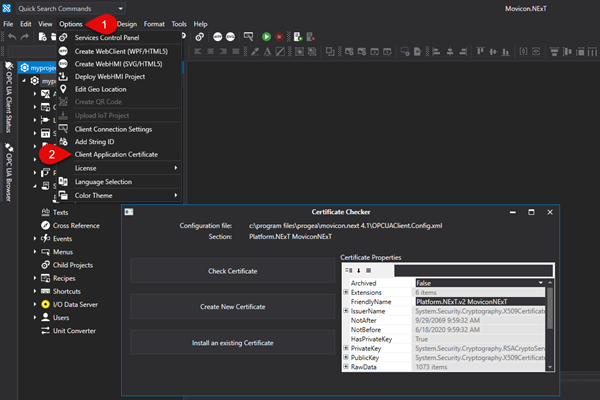
The certificated of Movicon.NExT Client side called "Platform.NExT.v2 MoviconNExT" can be checked, renamed or replace by using the configuration tool accessible from the menu > option and selecting the Application Certificate (2) item.